Well written, and it echoes my story as well..!
My Poems
Life 2
It’s almost the end of February, but there has been no clear response yet.
What my life would be after 4 months is still an enigmatic and elusive. Flummoxed with my current position, not been able to concentrate on other things properly…
Being very tardy in my work at present, and also almost shunning away the things that come across…
Yet, I always try to confront the situations with fortitude but nevertheless at times I get distraught…
Hope is actually a good thing, but my situation is like hoping against the hope.
My mind always sets a question that would I continue doing research in cutting edge and pursue my interests in research career in wireless communications/networks or would I just end up doing something in disdain…
As always should try to avoid being stampede and maintain peace and calm……..!
Satya.
Life 1
Have been suffering with severe sore throat, and fever. Beside this, have many challenges to face. Have gazillion papers to read and work on my project. It’s been a tough week before many stumbling blocks ahead.
Life is becoming more and more erratic, and chaos. Not knowing where I would stand after four months.
Interested in doing cutting edge research in wireless communication/networks, and also wanted to incubate a company during the process. But the conditions and complications I come across doesn’t allow me to do so.
The worst thing that happened to me is having bit too low GPA, which stops me always in dictating my research interests.
Currently, suffering with two problems. One is sore throat which perhaps will alleviate in couple of days, the other is my research. The problem in the latter keeps on escalating as the days sped.
Anyway, all I can now do is just wait and watch…..
Need to learn being patient……….
Have read this somewhere “Good things happen to who wait”
Let come what may…………………
Satya.
Gigabit Passive Optical Networking (GPON)
Optical fibers have the capacity of 25 Tb Hz of bandwidth, which is almost 1000 times greater than RF (radio frequency) bandwidth. Light is kept in the fiber core by total internal reflection. This makes the fiber act as wave-guide.
Optical Fiber is used in Telecommunications as a medium/channel to carry the information. The information can traverse long-distance as the attenuation of the signal/information is very less which in contrast to the information traversed using RF.
Each Fiber can carry multiple channels using different wavelengths of light, this is called as Wavelength Division Multiplexing (WDM).
PON (Passive Optical Networking) is connection from one point to multiple points (P2M) using an optical splitter which is passive ( which does not consume any power) splits the signal into 2,4,8,16,32.. directions. A PON consists of an OLT (Optical Line Terminal) at the service provider at the central office and ONU (Optical Network Unit) which is a collection of ONT’s (Optical Network Terminal) at the consumer end.
The word GPON which is Gigabit Passive Optical Networking is evolved from BPON (Bandwidth Passive Optical Networking). Gigabit is the speed/rate of the information carried on the Fiber i.e., the rate of the information is in GigaHertz….
The data is transmitted from OLT to ONT i.e., in downstream as a broadcast manner but encryption (AES) Advanced Encryption Standards is used to prevent eavesdropping and as TDMA manner from ONT (users) to OLT.
At ONT the light (optical signal) is converted into electrical signal. Each ONT has many ports like say Ethernet, VOIP, IPTV, etc i.e., a single fiber at the end user provides many services. It is usually referred as FTTU/FTTH (FTTX) fiber to the user/home.
GPON key technology.
OLT identifies ONT’s using ONU-ID (Identifier) which is 8 bit identifier and it is unique.
ALLOC_ID is a 12-bit number that the OLT assigns to an ONU to identify a traffic-bearing entity that is a recipient of upstream bandwidth allocations within that ONU. This traffic-bearing entity is also called T-CONT.
A Transmission Container (T-CONT) is an ONU object representing a group of logical connections that appear as a single entity for the purpose of upstream bandwidth assignment on the PON.
will keep posting more…
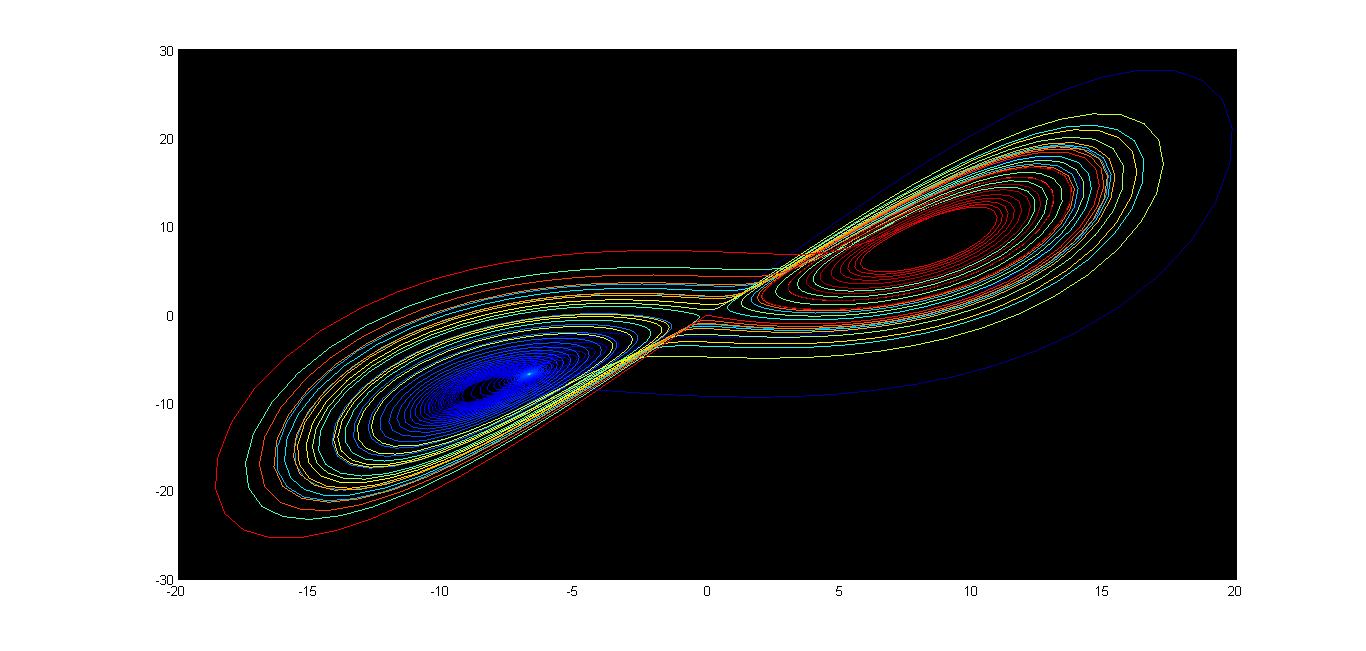
Lorenz attractor
The Lorentz attractor is generated by a set of differential equations which model a simple system of convective flow. In a paper published in 1963, Edward Lorentz demonstrated that this system exhibits chaotic behavior when the physical parameters are appropriately chosen.
The Lorenz system is deterministic, which means that if we know the exact starting values of variables then in theory we can determine their future values as they change with time. Lorenz demonstrated that if we begin this model by choosing some values for x, y, and z, and then do it again with just slightly different values, then you will quickly arrive at fundamentally different results. In real life we can never know the exact value of any physical measurement, With these results, Lorenz shocked the mathematical and scientific community by showing that a seemingly nice system of equations could defy conventional methods of prediction. This is called chaos, and its implications are far-reaching, especially in the field of weather prediction.
The Lorenz attractor is an example of a strange attractor. Strange attractors are unique from other phase-space attractors in that one does not know exactly where on the attractor the system will be. Two points on the attractor that are near each other at one time will be arbitrarily far apart at later times. The only restriction is that the state of system remain on the attractor. Strange attractors are also unique in that they never close on themselves — the motion of the system never repeats (non-periodic). The motion we are describing on these strange attractors is what we mean by chaotic behavior.
The set of equations describing this behavior are:
x’ = σ(y – x)
y’ = x(r – z) – y
z’ = xy – bz
where the three parameter σ , r, b are positive and are called the Prandtl number, the Rayleigh number, and a physical proportion, respectively. It is important to note that the x , y , z are not spacial coordinate. The ”x is proportional to the intensity of the convective motion, while y is proportional to the temperature difference between the ascending and descending currents, similar signs of x and y denoting that warm fluid is rising and cold fluid is descending. The variable z is proportional to the distortion of vertical temperature profile from linearity, a positive value indicating that the strongest gradients occur near the boundaries.
when σ=10, r<1, and b= 8/3 is chosen the plot look like this
when σ=10, r=1, and b= 8/3 is chosen the plot look like this
when σ=10, r>1, and b= 8/3 is chosen the plot look like this
when σ=10, r=28, and b= 8/3, the Lorenz system has chaotic solutions (but not all solutions are chaotic). The set of chaotic solutions make up the Lorenz attractor, a strange attractor
The Lorenz attractor is difficult to analyze, but the action of the differential equation on the attractor is described by a fairly simple geometric model.
Hadoop!
Hadoop is a free, Java-based programming framework that supports the processing of large data sets in a distributed computing environment. Hadoop makes it possible to run applications on systems with thousands of nodes involving thousands of terabytes. Facebook and Linkedin currently use Hadoop framework. Hadoop was first introduced by Google! Hadoop is primarily based on HDFS (Hadoop Distributed File System) and Map Reduce.
HDFS works like a normal distrubuted file system where a cluster is distributed across different nodes. There is a name node which has all the information about the data in other nodes called data nodes. The name node and data nodes are interconnected. After accomplishment of given job, the data nodes report at the name node. The end-user collect the information/result from the name node. The data nodes contains redundant data which can be used later if there is any node failure in one data node or in the other. What if the name node itself fails? How do we access the data? So this problem can be solved using Map reduce.
MapReduce is the key algorithm that the Hadoop MapReduce engine uses to distribute work around a cluster. The key aspect of the MapReduce algorithm is that if every Map and Reduce is independent of all other ongoing Maps and Reduces, then the operation can be run in parallel on different keys and lists of data. A distributed filesystem spreads multiple copies of the data across different machines. This not only offers reliability without the need for RAID-controlled disks, it offers multiple locations to run the mapping. If a machine with one copy of the data is busy or offline, another machine can be used. A job scheduler keeps track of which MR jobs are executing, schedules individual Maps, Reduces or intermediate merging operations to specific machines, monitors the success and failures of these individual Tasks, and works to complete the entire batch job. In this way the data can be accessed by people using programs to read and write data.
A snippet on Cognitive Radio
Radio spectrum resource is of fundamental importance in wireless communications. Nowadays, the access to radio spectrum is largely based on fixed spectrum allocation principle. With the deployment of more wireless applications/services, most of the available spectrum has been well allocated, thus
many countries are facing the problem of spectrum scarcity. On the other hand, measurement studies have revealed that most of the allocated spectrum experiences low utilization efficiency. These two facts motivate the introduction of dynamic spectrum access, which allows secondary users to use/share
the same radio spectrum originally allocated to the primary (licensed) users.
So, Cognitive radio which evolves from the Software Defined Radio is the enabling technology for dynamic spectrum access. The essential components in a cognitive radio system include spectrum sensing, cognitive medium access control and cognitive networking. That is Cognitive Radio is a transceiver which automatically detects the available channels in wireless spectrum and accordingly changes transmission or reception parameters. Cognitive radio is an artificial intelligence imposed on Software Defined Radio.
God must be awesome!
Once upon a time, a man was resting under the shade of a walnut tree on a hot, sultry afternoon. Just nearby was a pumpkin creeper. The man thought to himself, “Why would God grow pumpkins on a creeper and walnuts on a tree when it should have been the other way round? Pumpkins need stronger support while walnuts do not- how did it not occur to God?”. Just when he was about to leave the shady tree, a walnut fell from above and hit his head. He then realised that had it been pumpkins that grew on trees instead of walnuts, he’d be dead and that shady trees would not be safe for tired travellers, like himself, to rest under! He then realised that there’s a lot that God knows and we do not. He realised that God has planned everything beforehand.
God is a master-planner and everything on this Earth has a purpose.
#http://shehlarashid.com
Little of me!
Let only that little be left of me
whereby I may name thee my all.
Let only that little be left of my will
whereby I may feel thee on every side,
and come to thee in everything,
and offer to thee my love every moment.
Let only that little be left of me
whereby I may never hide thee.
Let only that little of my fetters be left
whereby I am bound with thy will,
and thy purpose is carried out in my life—and that is the fetter of thy love.
# Rabindranath Tagore
Code Division Multiple Access
3G? What is 3G? On what Technology it is based on? 3G is the third generation in cellular technology, which purely depends on CDMA200 though 2G also uses CDMA IS-95, the CDMA used in 3G is much more sophisticated than CDMA in 2G. So now the question is what is CDMA? Unlike FDMA (frequency division multiple access) and TDMA (time division multiple access), CDMA is much more sophisticated modulation!! oh sorry its not a modulation, its a technique used for multiple access at the same time using codes. Its completely based on spread spectrum technology, this can be done using either Direct Sequence Spread Spectrum (DSSS) or Frequency Hopping Spread Spectrum (FHSS). FHSS is mainly used in military defence and its a complex animal at the first. So, here I deal with DSCDMA which is Direct Sequence Code Division Multiple Access.
Direct Sequence Code Division Multiple Access:
In CDMA each user gets unique codes which then using the same code they can retrieve the data coming from the base station. So I guess you have a doubt with the codes? what are codes? okay let me tell you what these codes are, these are pseudo random codes. Confused? well let me comprehend about this. These codes are randomly generated bit streams of 1 and -1, which when looked looks like noise but since its not a noise lets give it a name as pseudo noise. Yes, these are called PN codes. Now lets get into more detailed description of CDMA.
Now say we have a bandwidth (BW) B Hz, then the time taken for each bit to be transmitted will be how much ? yes it is 1/B seconds. Now as we are transmitting a bit in the form of codes (say N sequence code) and to transmit the date at the same bit rate we need to increase the bandwidth as each symbol of the bit should be sent at 1/NB seconds so we need NB Hz bandwidth.
CDMA transceiver :
At the transmitter the data is merged with the codes generated using some techniques (will be discussed later) and transmitted to the channel. Now the data at the transmitter looks like a noise i.e., the information of the signal is mingled with the noise floor, so now the problem is how do we retrieve the transmitted data? So, to retrieve the data the receiver must know the code that was generated at the transmission side, once the codes are known the information (data) can be retrieved by performing the corss-correlation using the known code and the received data. Thus you have the transmitted data.
Generation of codes :
To keep the overall bit rate same the bit rate of codes has to be increased as a consequence of this the bandwidth will increase, so as these codes are increasing the bandwidth i.e., these codes spread the data over the entire bandwidth, they are called as spreading codes and each bit in code is called as chip and the bit rate of chips (codes) is called chip rate.
The spreading factor is defined as the ratio of Chip rate to the Symbol rate(data rate).
The codes used in the CDMA are :
- PN Codes
- Walsch codes
- Gold codes and etc..
Here I discuss the above first two codes, they are PN codes and Walsch Codes.
PN codes:
PN codes as said before they are pseudo-random noise codes, generated using a -1 and 1’s in NRZ form, 0 and 1’s in polar form. These PN codes are generated using Linear Feedback Shift Register (LFSR). A typical LFSR is shown below.
The number of 0’s and 1’s thus generated in PN code must always be 1. The PN codes has very good auto-correlation but not that good cross-correlation i.e., the correlation is not equal to zero at different lags.
Walsch codes:
Walsch codes are generated using Hadamard Matrix. These codes generated are orthogonal to each other. They have bad auto-correlation and good cross-correlation, so many users can be allowed at the same time. But because of mutlipath interference, there would be a delay in the signal, as a consequence of this it looses its orthogonality and can no longer be used. In that case PN codes are preferred to Walsche codes.
Walsch code are generated as follows,
let H1= [1]
then H2=[ H1 H1 ]
[ H1 H1bar].
for futher details on walsch codes and on CDMA follow the links given below…